Get a mobile app that is compliant with all SCA & dynamic linking requirements, offering an enhanced level of security and seamless user experience.
SCA & dynamic linking
Mitigate fraud risks in a compliant way

The PSD2 mandates SCA procedures to be applied when accessing accounts online and for initiating payments. The scope of SCA and dynamic linking is to improve the security of payment experience, minimise fraud risk, and guarantee customer protection.

The RTS on SCA implies that the end-customer's identity must be verified using at least two of the following authentication methods: knowledge, possession and inherence. Each element must be independent, so that the breach of one element will not compromise the others. Dynamic linking represents a security element for payments and is realised through the generation of an authentication code that is linked to payment amount and payee of transaction.
Request a demoHow it works
When compliance meets customers' convenience
Growth in online and mobile payments has been followed by an online fraud boom. Every customer expects convenience but doesn’t want to lose security during the payments or mobile banking operations, that is why Mobile SCA becomes a genuine solution to meet all the needs.
About Mobile SCA
Deliver a frictionless authentication experience
Salt Edge has developed the Mobile SCA application to handle dynamic linking and meet the strong customer authentication requirements. The solution simplifies the access to banks’ and EMIs’ digital channels, granting a user-friendly and secure authentication and authorisation process.
Salt Edge Mobile SCA combines the world's best UX and security practices to offer you a solution that makes your business and customers' payment experience much better and safer.
Open Banking Compliance
Become fully open banking compliant in just 1 month
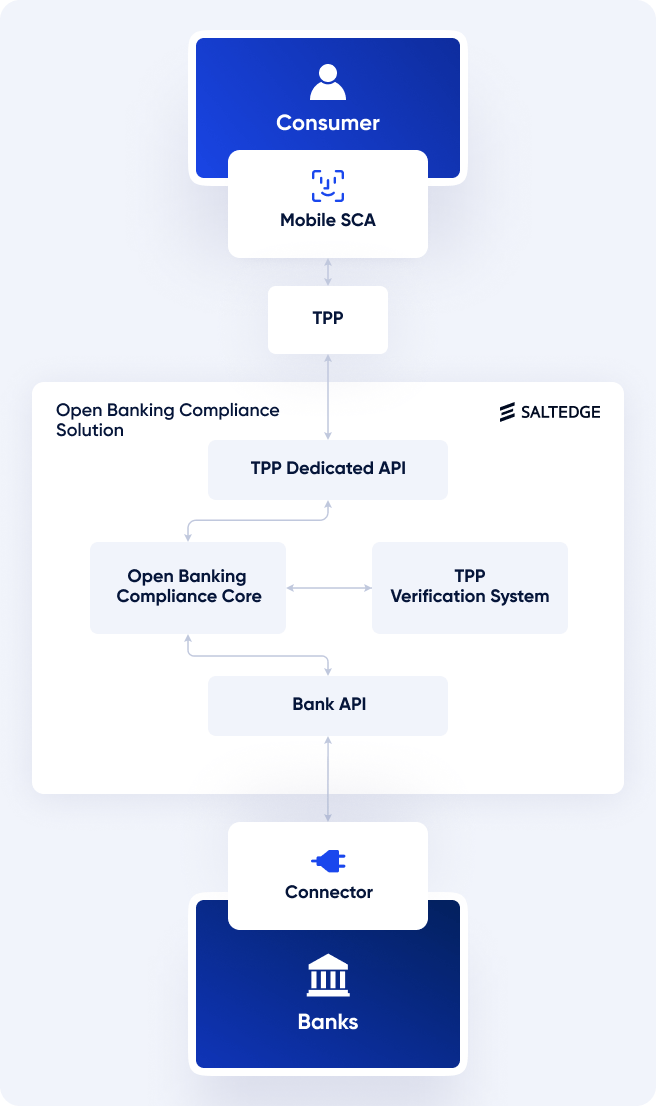
Mobile SCA is built to secure digital access and is also available as a component of the comprehensive Salt Edge Open Banking Compliance Solution. Being a cost-effective and reliable SaaS solution, Salt Edge Open Banking Compliance offers a targeted approach that strikes the right balance between security and user convenience, requiring minimum technical participation from the ASPSP’s side.
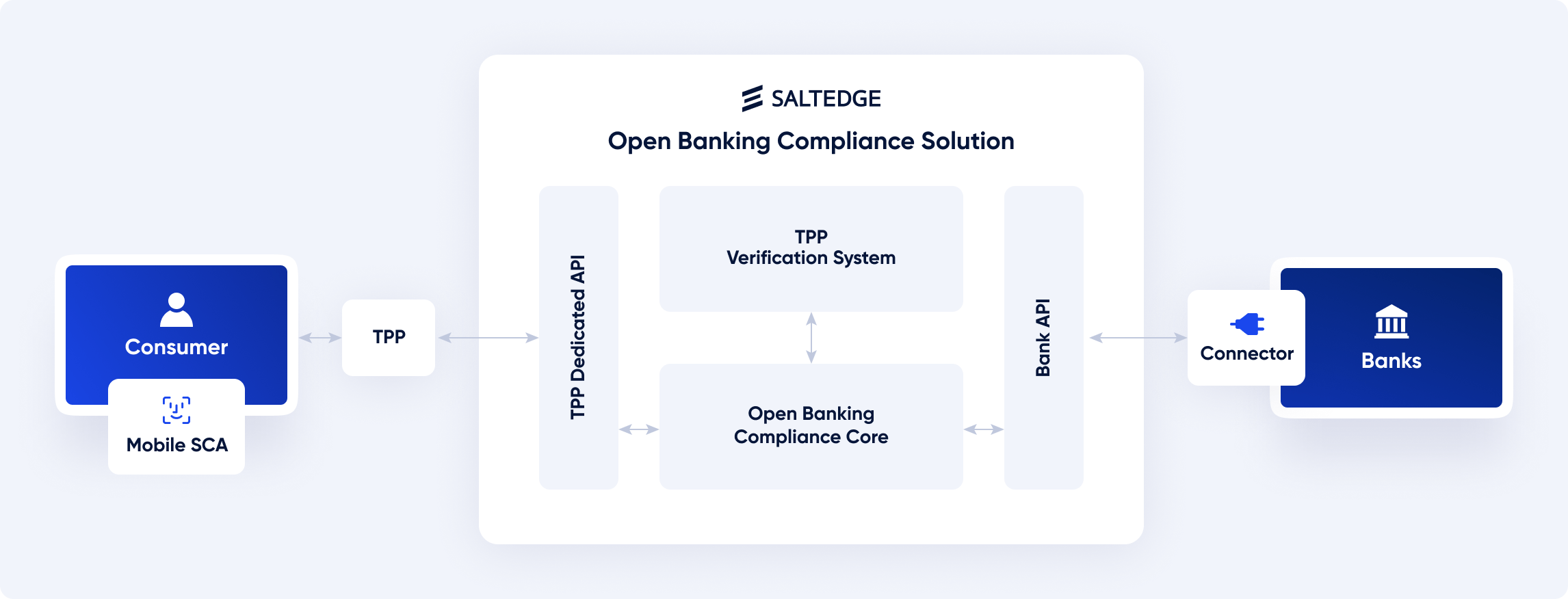
Use cases
Secure, compliant and seamless
SCA experience for
Benefits
Perfect match between safety and convenience






They trust Salt Edge










